Online Forums
Technical support is provided through Support Forums below. Anybody can view them; you need to Register/Login to our site (see links in upper right corner) in order to Post questions. You do not have to be a licensed user of our product.
Please read Rules for forum posts before reporting your issue or asking a question. OPC Labs team is actively monitoring the forums, and replies as soon as possible. Various technical information can also be found in our Knowledge Base. For your convenience, we have also assembled a Frequently Asked Questions page.
Do not use the Contact page for technical issues.
Self-signed certificate to apply
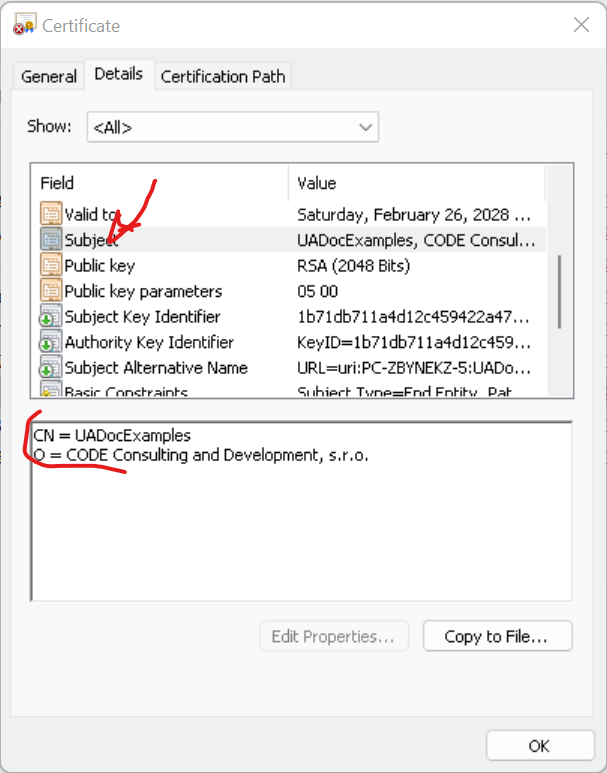
what QuickOPC (but, in fact, all UA applications I know) is using to find the right certificate in the certificate store is the "Subject Name". This is a so-called X509 distinguished name, which a series of one or more elements. It can also be expressed as a string, e.g. "CN=UADocExamples, O=CODE Consulting and Development, s.r.o.". The order of the element matters. It should be read as an instructions to look up in a directory service, read from right to left: In the example I gave, first find the organization given by the "O=...", then in this organization, find something with "common name" given by the "CN=..." part.
The subject name is *inside* the certificate, and in general case it is unrelated to the file name of the certificate.
To find out the subject name of the auto-generated (or some other) certificate, find the certificate-s .DER file in Windows, and double-click on it, the switch to the Details tab, and find the "Subject", as on the following picture:
If you are generating the certificate on your own, you need to instruct your tool to use the precise subject name you need. In addition, OPC UA specs put other requirements on certificate for UA application. For example, the Application URI needs to go to "Subject Alternative Name" (this also can be seen on the picture above). And there may be other requirements (see UA specs); failing to fulfill them will most likely result in the certificate being rejected, sometimes without an option to override that.
The naming scheme that QuickOPC (and some other UA apps) use for certificate in file-based certificate store is that it starts with the "common name", which is the "CN=" part from the subject name, and it is then followed by a certificate thumbprint in [ ] brackets (think of a thumbprint as a checksum). It should *not* be necessary to follow this naming scheme for your own certificate - even if it will look differently from all other files in that directory. What is used for finding the certificate is the subject name inside the certificate (i.e. QuickOPC needs to load *all* files to "look inside" for them), as described above. Your file name may be just about anything, so you do not need to worry about replicating the naming scheme correctly.
If you change the subject name inside your certificate to precisely the one used by the default auto-generated certificate, then there is no code change needed inside your program. That is the recommended approach.
For a different name, what needs to be changed - before performing any OPC operation in the program - is the value of EasyUAClient.SharedParameters.EngineParameters.ApplicationParameters.ApplicationManifest.InstanceCertificateSubject, to a string with syntax like "CN=UADocExamples, O=CODE Consulting and Development, s.r.o.".
Regarding where to put the certificate: What you have written looks most likely correct. In some cases, applications built for .NET Core/.NET 5+ may use "local" directory stores - in which cases you will such certificate directory structure under the directory where the .EXE of your program is. If such structure is not there (after running the program), then it is using the common folder you have identified.
Best regards
Please Log in or Create an account to join the conversation.
- Regarding your point to change my own generated certificate subject name to the auto-generated subject name;
The auto-generated certificate of QuickOPC client starts with a name that is related to my application and then a random code (seems like) inside the square bracket. In my case it is like for example ABC [FB5D997D6485684F77673D9A4C023D280B9EE94A].der. Now my questions are 1- will the random code inside the bracket change every time I restart my application that contains QuickOPC client? I might be wrong but I would think I have seen sometimes a different random code inside the bracket (as I said I am not sure about this) 2- Will the code inside the bracket (or more correctly the subject name) of the certificate for both parts .der file and .pfx file the same? 3- If I change the subject name of my own generated one to the auto-generated subject name, would I still need to instruct Quick OPC to use it or will it just work?
- Regarding if I have the subject name of my own;
Please point me to more info on how to instruct QuickOPC to use it.
- Regarding where to put the certificates;
In my Windows 10 PC, I have two folders in the OPC Foundation forlder (in C drive in CertificateStores). One MachineDefault and the other UA Applications. The store of "own" certificate where QuickOPC takes it from will be UA Applications folder and store for "Trusted peer" certificate is MachineDefault folder, am I correct?
Best regards.
Please Log in or Create an account to join the conversation.
If you generate the certificate for QuickOPC yourself, the main thing to watch for is the subject name. You should either
a) examine the auto-generated certificate and take the precise subject name from it (this is the recommended, because easier and less error prone way), or
b) choose your own subject name, and then instruct QuickOPC to use it (I can point you to more info about this if you request).
The next thing is where to put the certificate. It should go into two two stores:
1) the store for "own" certificates - this is where QuickOPC will take it from - this story will have the .DER part and then, in the "private" folder, the cert with the private key in the PFX format, and
2) the store for "trusted peer" certificate (I repeat: not the "trusted issuers") - because QuickOPC will also validate its own certificate, and it needs to trust it too.
See:
- opclabs.doc-that.com/files/onlinedocs/QuickOpc/Latest/User%2...0Client-Server%20Security.html
- opclabs.doc-that.com/files/onlinedocs/QuickOpc/Latest/User%2...%20Instance%20Certificate.html
- opclabs.doc-that.com/files/onlinedocs/QuickOpc/Latest/User%2...ry%20Certificate%20Stores.html
If you have a client certificate all set up correctly, and you then try to make a secure connection to a server while the mutual trust has not yet been established (which you can do by placing the other-party certs to the right stores too), two things then typically happen (both of them!):
1) The server does not trust the client. It rejects its certificate and puts it into its "rejected" folder. By moving it to trusted peers it can be made trusted.
2) The client does not trust the server. It rejects its certificate and puts it into its "rejected" folder. By moving it to trusted peers it can be made trusted.
Only after all of this is properly done, the secure connections will work as they should.
Regards
Please Log in or Create an account to join the conversation.
I did this because the auto-generated certificates of QuickOpc has one year validity and this might halt the software that we are going to install for our customer over the years. So we should revalidate it every year. The ssl self-signed that I have created very long lasting self-signed certificate to use for this. I have used this cert in .der format.
So can we extend the expiration date of QuickOpc auto-generated certificate for 20 years (or longer) for example?
Best regards.
Please Log in or Create an account to join the conversation.
You will need two certificates. You cannot reuse the same one for both server and client (technically it might be possible to make it work, but it is totally against the OPC UA rules, and insecure).
Why precisely are you creating the certificate for the QuickOPC side by yourself? I am asking this before we go further, because in fact you do not have to do this at all. QuickOPC will create such certificate automatically (self-signed). It will have reasonable defaults, and you can even change those using some parameters that we have. So please first answer this - because using the auto-generated certificate is easier than tying the QuickOPC to an existing "external" certificate.
Best regards
Please Log in or Create an account to join the conversation.
The Opc server I have is Opc Foundation server. And like I mentioned OpcUa client is a QuickOpc based client. I have both OpcUa client and OpcUa server running on the same PC. So if I can make my OPC server to use the generated ssl self-signed certificate that I have, then when the OpcUa client connects to the server, it will receive the certificate from the server. The client will then check if this certificate is valid by checking the PC for certification Authorities (where I have added the certificate to the Trusted Root Certification Authorities) that matches the stamp (signed) from the certificate. Does this make sense to you?
Another thing is that; the key is password protected but I can export it with the password I have (I mean I can decrypt it and then use it on the client side if QuickOpc does not support the password protected cert.)
I have generated one self-signed certificate. With the expalnation above that I have two sides (both client and server on one PC) where and how this certificate should be placed?
Best regards.
Please Log in or Create an account to join the conversation.
On each server side, how it is done depends on the server, but generally the self-signed client certificate needs to appear in something that has the meaning of the "trusted peers" as well.
However, QuickOPC does not currently support password-protected private keys, so in this sense you cannot do what you are asking for. Private key password protection will be available in version 2023.1.
More info:
opclabs.doc-that.com/files/onlinedocs/QuickOpc/Latest/User%2...0Client-Server%20Security.html
Best regards
Please Log in or Create an account to join the conversation.
I have used ssl to create a self-signed certificate (password protected) that last for very long years (this is because the opc server I am using auto-generates certs that are valid for one year only).
I have added the generated cert to the windows to the Trusted Root Certification Authorities, but I have to add that to the Opc server (or the Opc client side) to make this certificate to be used by Opc server. My Opc client is QuickOpc. (a sidenote here; this is just my understanding, for me to take this certificate to distribute to all PCs that I am going to install my Opc client on, it's better to include the self-signed cert as part of the Opc client solution (.Net based solution), Do you agree?)
But my main question is how to add this self-signed certificate that is password protected to the Opc server and/or to the Opc client solution?
Best regards.
Please Log in or Create an account to join the conversation.